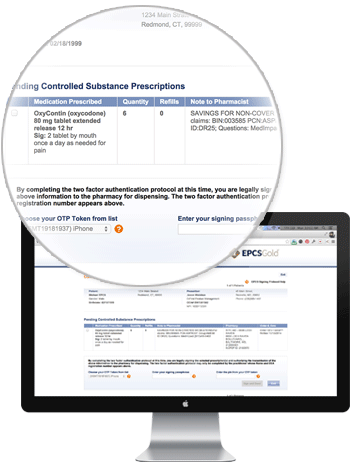
EPCSGoldSM enables clinical staff to quickly and easily identify doctor shoppers to ensure the right medications get to the right patient. Controlled substance e-prescribing is growing at a phenomenal rate, bolstered by government and healthcare industry awareness that electronically prescribing controlled substances is a first-line defense against the nation’s prescription drug abuse epidemic. Providers in every U.S. state can now actively e-prescribe controlled substances through independent pharmacies as well as with national drug chains like Rite-Aid, Walgreens, and CVS.
EPCSGold was the first controlled substance e-prescribing solution in the country. Today, EPCSGold is integrated within more than 260 EMR/EHR/HIS systems. When combined with Rcopia discharge e-prescribing, EPCSGold presents a seamless, easy-to-use electronic prescribing workflow for both legend drugs and controlled substances.
EPCSGoldSM Benefits Include:
- Eliminating potential transcription and pharmacy errors
- In-workflow PDMP checking
- Reduced risk of fraud and abuse by eliminating paper prescription pads
- Clinical and drug interaction alerts and formulary information
- Automated clinical decision support, including dosage checking and duplicate therapy alerts